News
How Machine Learning and Semantic Embeddings Reorder CVE Vulnerabilities Beyond Raw CVSS Scores
 2+ hour, 8+ min ago (243+ words) We install and load all required NLP, machine learning, and visualization libraries for the end-to-end pipeline. We ensure the runtime is fully self-contained and ready to execute in Colab or similar notebook environments. It establishes a reproducible foundation for the…...
2+ hour, 8+ min ago (243+ words) We install and load all required NLP, machine learning, and visualization libraries for the end-to-end pipeline. We ensure the runtime is fully self-contained and ready to execute in Colab or similar notebook environments. It establishes a reproducible foundation for the…...
A Coding Guide to Demonstrate Targeted Data Poisoning Attacks in Deep Learning by Label Flipping on CIFAR-10 with PyTorch
 1+ week, 5+ day ago (294+ words) We set up the core environment required for the experiment and define all global configuration parameters in a single place. We ensure reproducibility by fixing random seeds across PyTorch and NumPy. We also explicitly select the compute device so the…...
1+ week, 5+ day ago (294+ words) We set up the core environment required for the experiment and define all global configuration parameters in a single place. We ensure reproducibility by fixing random seeds across PyTorch and NumPy. We also explicitly select the compute device so the…...
A Coding Implementation of an OpenAI-Assisted Privacy-Preserving Federated Fraud Detection System from Scratch Using Lightweight PyTorch Simulations
3+ week, 3+ day ago (259+ words) We set up the execution environment and import all required libraries for data generation, modeling, evaluation, and reporting. We also fix random seeds and the device configuration to ensure our federated simulation remains deterministic and reproducible on CPU. Check out…...
AI Interview Series #2: Explain Some of the Common Model Context Protocol (MCP) Security Vulnerabilities
 2+ mon, 1+ week ago (162+ words) A Tool Poisoning Attack happens when an attacker inserts hidden malicious instructions inside an MCP tool's metadata or description. A Tool Hijacking Attack happens when you connect multiple MCP servers to the same client, and one of them is malicious....
2+ mon, 1+ week ago (162+ words) A Tool Poisoning Attack happens when an attacker inserts hidden malicious instructions inside an MCP tool's metadata or description. A Tool Hijacking Attack happens when you connect multiple MCP servers to the same client, and one of them is malicious....
A Coding Guide to Build an AI-Powered Cryptographic Agent System with Hybrid Encryption, Digital Signatures, and Adaptive Security Intelligence
 3+ mon, 6+ day ago (193+ words) We begin by importing all necessary libraries for cryptography, AI-based analysis, and data handling. We also define a SecurityEvent dataclass to record and analyze all important events in the cryptographic system. Check out the'FULL CODES here. We define the CryptoAgent…...
3+ mon, 6+ day ago (193+ words) We begin by importing all necessary libraries for cryptography, AI-based analysis, and data handling. We also define a SecurityEvent dataclass to record and analyze all important events in the cryptographic system. Check out the'FULL CODES here. We define the CryptoAgent…...
A Coding Implementation of Secure AI Agent with Self-Auditing Guardrails, PII Redaction, and Safe Tool Access in Python
 3+ mon, 1+ week ago (185+ words) We begin by setting up our security framework and initializing the optional Hugging Face model for auditing. We define the key constants, patterns, and rules that govern our agent's security behavior, ensuring every interaction follows strict boundaries. Check out the'FULL…...
3+ mon, 1+ week ago (185+ words) We begin by setting up our security framework and initializing the optional Hugging Face model for auditing. We define the key constants, patterns, and rules that govern our agent's security behavior, ensuring every interaction follows strict boundaries. Check out the'FULL…...
Google DeepMind Introduces CodeMender: A New AI Agent that Uses Gemini Deep Think to Automatically Patch Critical Software Vulnerabilities
 3+ mon, 2+ week ago (431+ words) What if an AI agent could localize a root cause, prove a candidate fix via automated analysis and testing, and proactively rewrite related code to eliminate the entire vulnerability class'then open an upstream patch for review? Google DeepMind introduces CodeMender,…...
3+ mon, 2+ week ago (431+ words) What if an AI agent could localize a root cause, prove a candidate fix via automated analysis and testing, and proactively rewrite related code to eliminate the entire vulnerability class'then open an upstream patch for review? Google DeepMind introduces CodeMender,…...
The Role of Model Context Protocol (MCP) in Generative AI Security and Red Teaming
 3+ mon, 3+ week ago (355+ words) The Authorization approach is unusually prescriptive for an integration protocol and should be enforced as follows: This is the core of MCP's security structure: model-side capabilities are powerful, but the protocol insists that servers be first-class principals with their own…...
3+ mon, 3+ week ago (355+ words) The Authorization approach is unusually prescriptive for an integration protocol and should be enforced as follows: This is the core of MCP's security structure: model-side capabilities are powerful, but the protocol insists that servers be first-class principals with their own…...
Delinea Released an MCP Server to Put Guardrails Around AI Agents Credential Access
 3+ mon, 3+ week ago (384+ words) Delinea released an Model Context Protocol (MCP) server that let AI-agent access to credentials stored in Delinea Secret Server and the Delinea Platform. The server applies identity checks and policy rules on every call, aiming to keep long-lived secrets out…...
3+ mon, 3+ week ago (384+ words) Delinea released an Model Context Protocol (MCP) server that let AI-agent access to credentials stored in Delinea Secret Server and the Delinea Platform. The server applies identity checks and policy rules on every call, aiming to keep long-lived secrets out…...
This AI Research Proposes an AI Agent Immune System for Adaptive Cybersecurity: 3.4× Faster Containment with
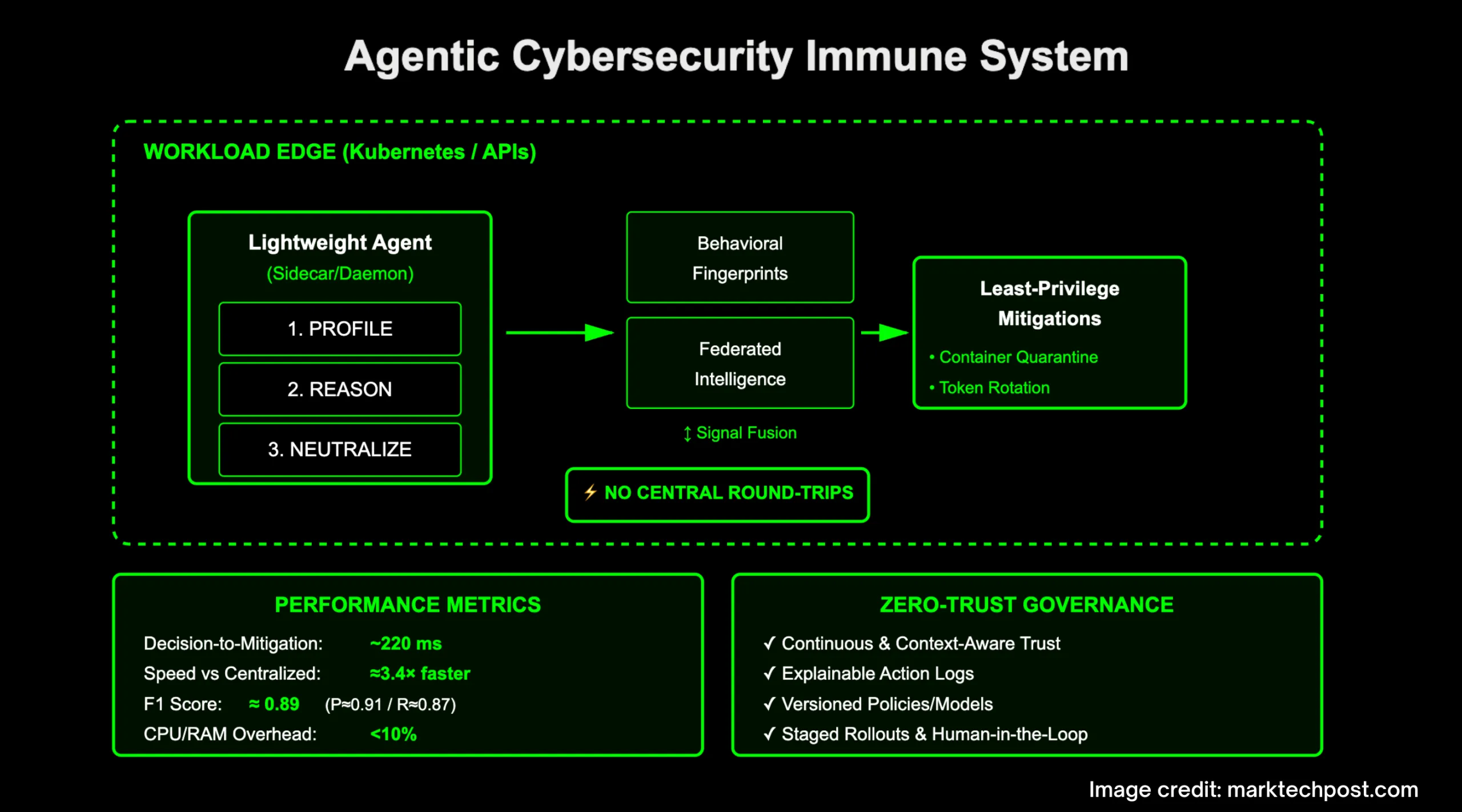 3+ mon, 3+ week ago (1051+ words) Can your AI security stack profile, reason, and neutralize a live security threat in ~220 ms'without a central round-trip? A team of researchers from Google and University of Arkansas at Little Rock outline an agentic cybersecurity "immune system" built from lightweight,…...
3+ mon, 3+ week ago (1051+ words) Can your AI security stack profile, reason, and neutralize a live security threat in ~220 ms'without a central round-trip? A team of researchers from Google and University of Arkansas at Little Rock outline an agentic cybersecurity "immune system" built from lightweight,…...